The Rogue Scholar science blog archive consolidated authentication into a single Identity and Access Management (IAM) service, powered by a self-hosted Keycloak instance, at the end of last year. This week, this service started supporting passwordless authentication via magic links.
Magic Link – A time-sensitive hyperlink sent by email, allowing the recipient to log in to a system without the usual authentication process. https://en.wiktionary.org/wiki/magic_link
The Rogue Scholar login form has not changed: you register an account via ORCID (and validate your email address), and you sign in via ORCID or email.
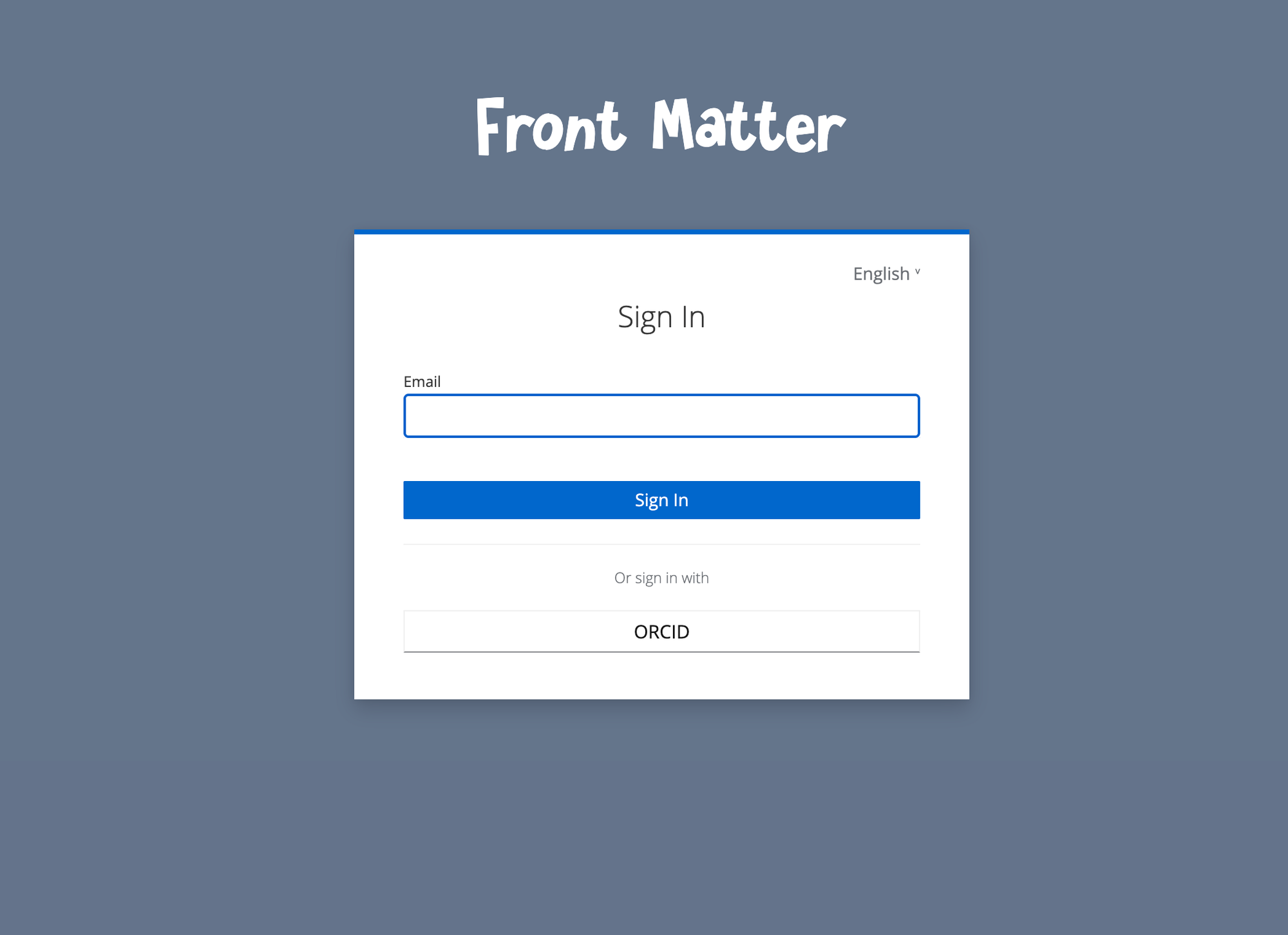
This week, the change is that instead of sending a six-digit code via email that you have to enter into another form, the email now contains a magic link that directly signs you in when you click on it.
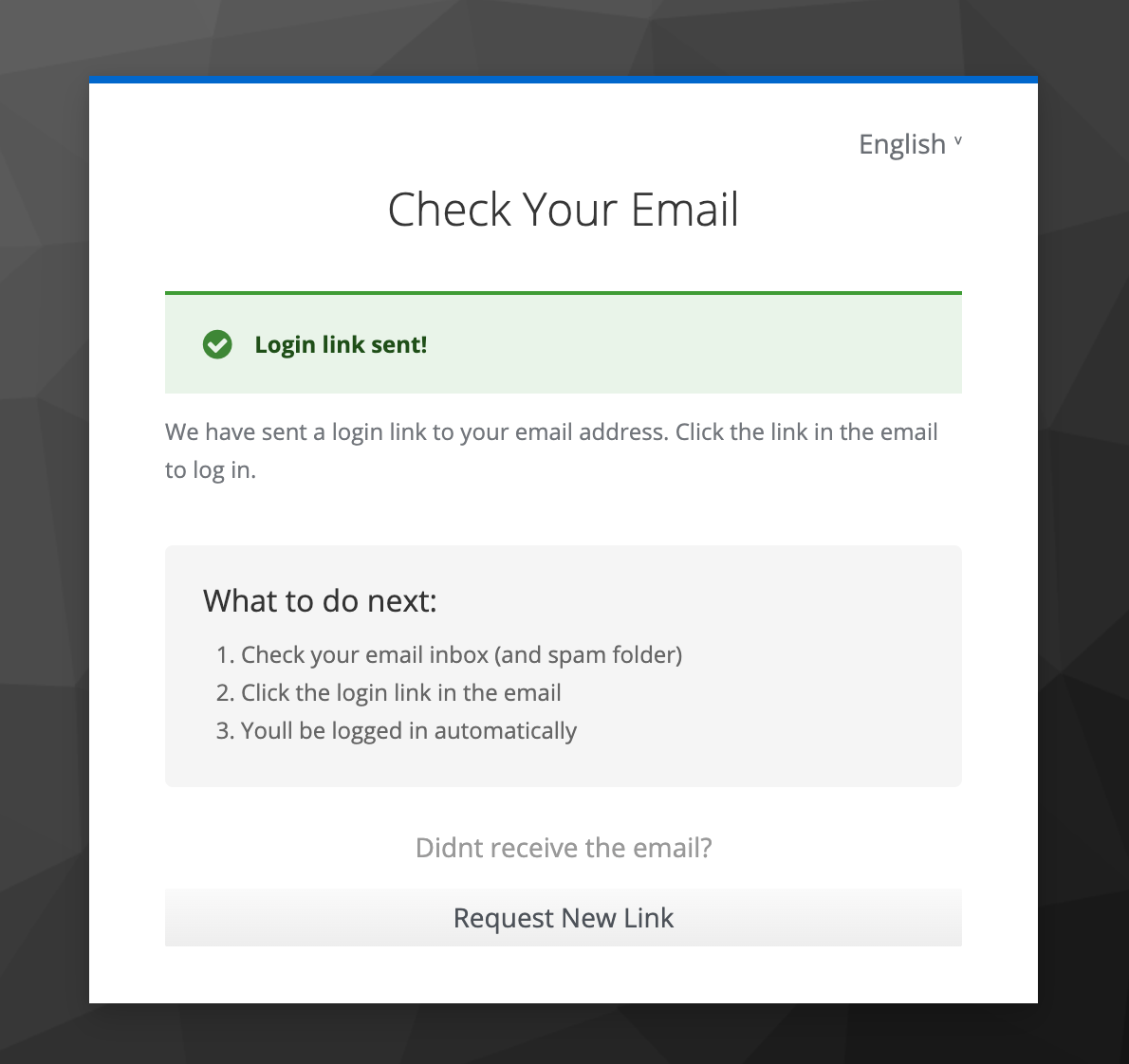
Magic links are a common way to authenticate users without passwords. They are less secure than passkeys (as theoretically anyone with access to your email can use them until they expire after 15 min), but are more secure than passwords, and have the big advantage over passkeys that no additional setup is required for the user – which might be confusing until passkeys are more widely adopted.
Authentication is always a balancing act between security and convenience. If you make authentication too simple, the system is not secure. If you make authentication too complicated, users will not use your system, or invent ways to bypass security that were not intended. Magic links provide a good balance for Rogue Scholar user accounts, and they are optional, as users can always authenticate via ORCID.
Unfortunately, it is very common to charge users more for better security, so implementing Identity and Access Management has additional challenges for self-hosted open source software such as Rogue Scholar, which depends on InvenioRDM, the turn-key data repository platform. Commercial IAM services typically charge by monthly active users, which is not a good fit for InvenioRDM instances once they become popular. Open source IAM solutions might either have limitations (e.g. Authentik requires an enterprise license for ORCID OIDC integration) or are too complicated to set up. Keycloak seems to be the best fit as an IAM solution for InvenioRDM.
One fundamental architecture decision is between building the core functionality of IAM into the repository platform or integrating with an existing open source solution. InvenioRDM supports many functionalities required for IAM out of the box, but for larger or more specialized InvenioRDM instances such as Rogue Scholar, using a dedicated and mature IAM solution makes sense.
Rather than building all desired IAM functionalities into InvenioRDM, we can rely on dedicated IAM software and its community to set up rules and workflows for new user registration. Who can register and what information must they provide? For Rogue Scholar, registration is open to all users (rather than invitation only), a valid email address and an authenticated ORCID are required, but the username will be generated by the system.
InvenioRDM has two levels of roles and permissions: general roles, such as admin user, and community-based roles and permissions. These roles and permissions are best handled by InvenioRDM, and InvenioRDM has a lot of functionality to support nuanced roles and permissions. Rogue Scholar for example has the requirement that all content and (almost) all metadata are generated by participating blogs – as it is an archive of science blogs – and therefore the built-in InvenioRDM editor is disabled for all users.
Keycloak is a very popular open source IAM solution that is often used by universities and research institutions. Keycloak doesn't support magic links out of the box, so Rogue Scholar is using a Keycloak extension for this functionality, together with three other Keycloak extensions, and bundled into a keycloak-invenio Docker image that can be deployed together with InvenioRDM.
You see from the screenshots above that more fine-tuning of the Keycloak forms is needed going forward, e.g. consistent backgrounds in all forms. keycloak-invenio uses keycloakify, which uses modern frontend tooling (e.g. React, Storybook) instead of Java Freemaker templates.
Please reach out via Slack, email, Mastodon, or Bluesky if you have any questions or comments regarding the new authentication service.
References
- Fenner, M. (2025, December 30). Consolidating Rogue Scholar Authentication. Front Matter. https://doi.org/10.53731/5q274-3e235


