Starting this week, the Rogue Scholar science blog archive has consolidated authentication into a single Identity and Access Management (IAM) service, powered by a self-hosted Keycloak instance at https://auth.front-matter.de.
The goal of this consolidation into a single service was to make it easier to enforce three basic rules:
- Authenticated users must have an ORCID identifier,
- Authenticated users must have a validated email address,
- Rogue Scholar doesn't store passwords for authenticated users.
Enforcing these rules is possible within the InvenioRDM repository platform that powers Rogue Scholar, but may require extensive work on Identity and Access Management, for example enabling passwordless accounts. For larger repositories it makes more sense to use a dedicated service for this, and Keycloak is one of the most popular open source software stacks for this purpose.
There are other open source solutions for this purpose, but they are either limited in functionality (e.g. Pocket ID provides passkeys but no other authentication workflows), or require a commercial licence for some functionality (e.g. Authentik when used with an external social login such as ORCID). Keycloak is already widely used by the InvenioRDM community, and I am using a customized Docker image (keycloak-invenio) built with four extensions:
- the keycloak-orcid identify provider extension to integrate Keycloak with ORCID via Open ID Connect (OIDC),
- the auto-username extension that automatically generates random usernames such as usr_3k8d9ma2 (using the same Crockford base32 encoding as InvenioRDM records),
- the 2fa-email- authenticator extension that sends an access code via email, so that users don't have to enter a password,
- keycloakify for customizing login, account, email, and administration pages.
The sign-in page currently looks like this, enabling account registration via ORCID and sign-in via ORCID or email:
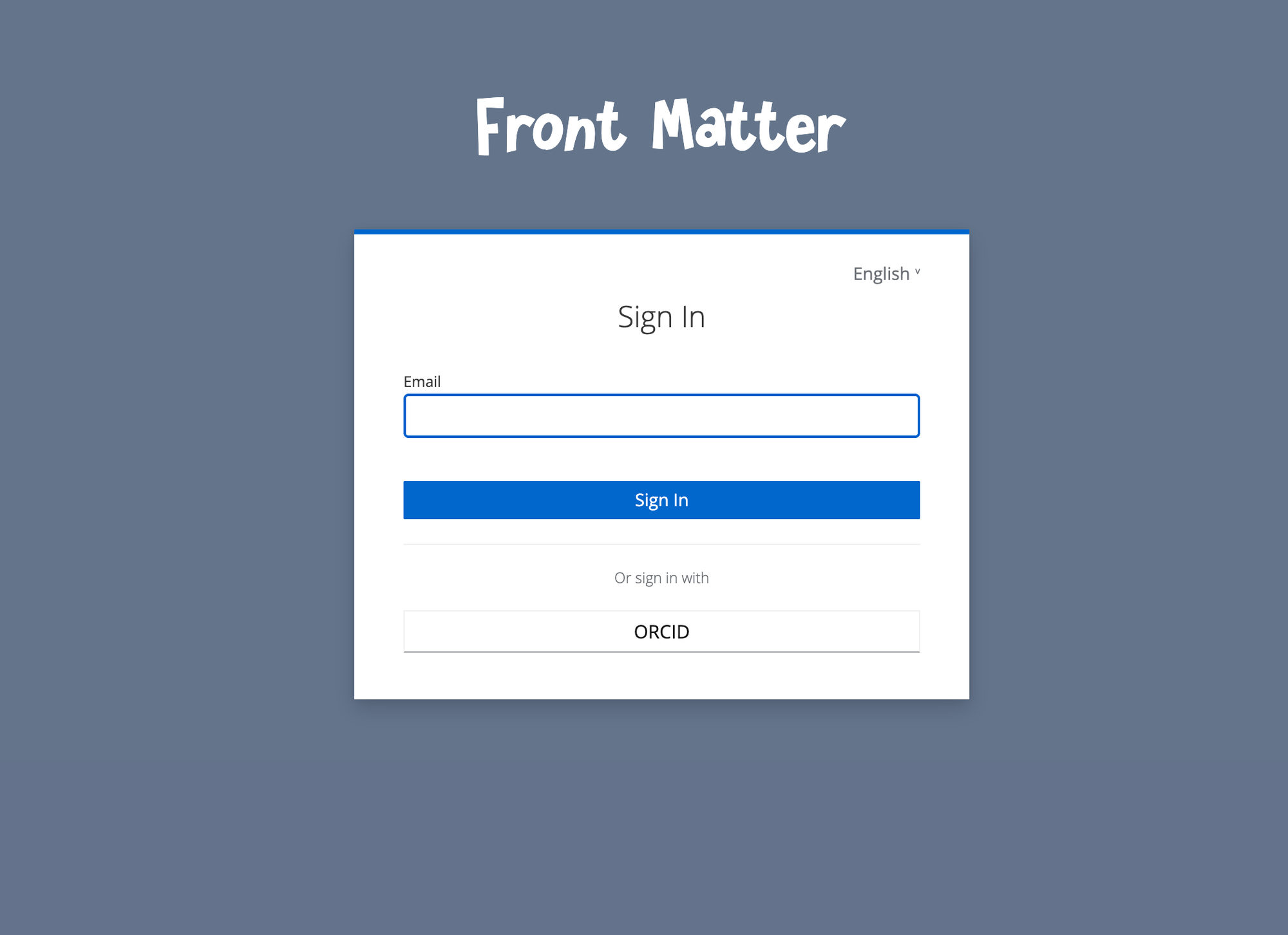
Usernames are automatically generated with the auto-username extension, meaning that existing accounts may not be reused and have to be linked manually.
Please reach out via Slack, email, Mastodon, or Bluesky if you have any questions or comments regarding the new authentication service.


